
Importing Authentik objects into Terraform
This is a super small note more for myself as i forget how to do this everytime ive wanted to do. There isnt really much documentation on the internet about how to import objects into Terraform whe...

This is a super small note more for myself as i forget how to do this everytime ive wanted to do. There isnt really much documentation on the internet about how to import objects into Terraform whe...

Over a year ago i built and LDO Voron V0.2 sold to me by 3djake.uk. It was my first venture into the Voron world although not my first time with a premium DIY kit. I have built and use a RatRig Vco...

Just thought this would be a good spot to introduce the first API i have built. Its currently hosted at grid-data.co.uk. It is quite a simple API with only a couple of endpoints at the moment, but...
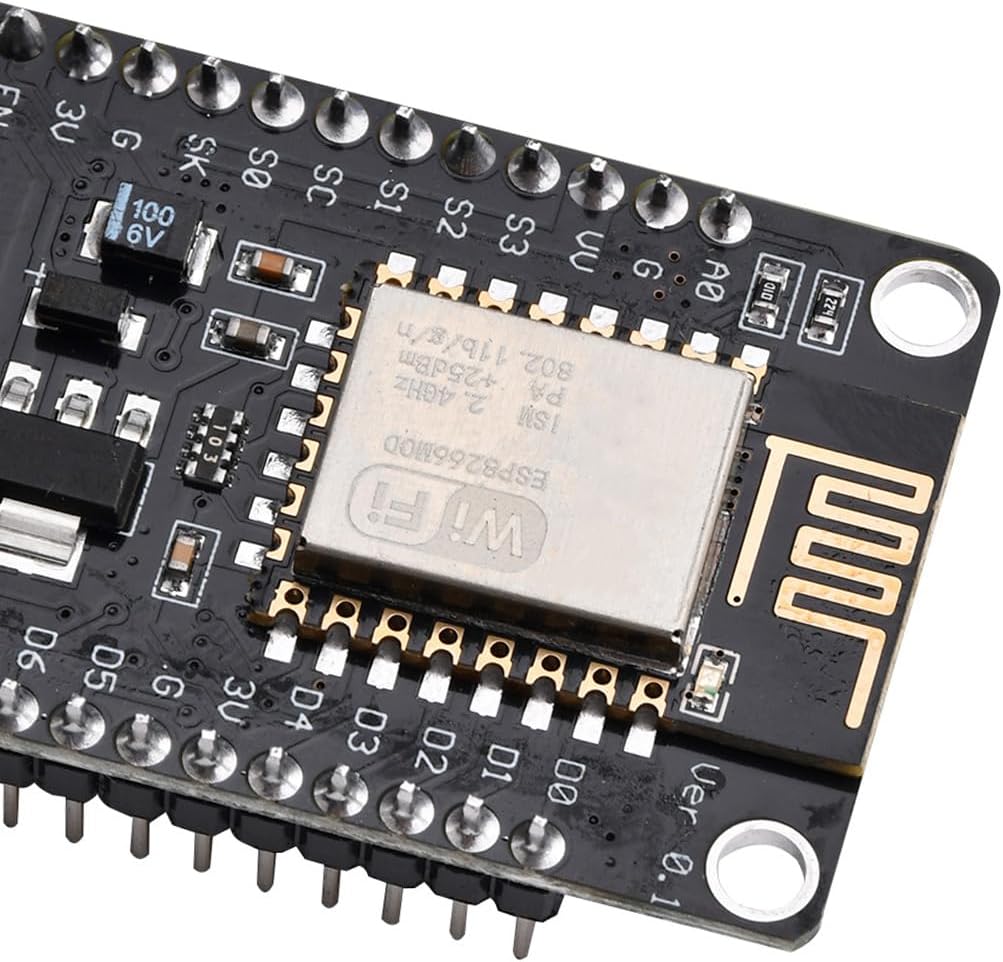
I recently bought a tortoise (named Burrito) as a little buddy in my office. He’s a cool dude, only about 18 months old so pretty small. Due to work and kid commitments i was struggling to remember...

- [Traefik](#traefik) - [Prometheus](#prometheus) - [Alertmanager](#alertmanager) - [Grafana](#grafana) - [Blackbox Exporter](#blackbox-exporter) - [Node Exporter](#node-exporter) - [Watc...
Ive recently had the unfortunate experience of working with this host after renting a dedicated server. This is how it went for me… The backstory This server was my Plex automation server. It ran...

This will hopefully be quite a quick run through on how i deploy this website to my VPS using 3 services: Visual Studio Code Server Github Circle-CI - [Visual Studio Code Server](#visual...
I am an avid Sim racer, i enjoy both engaging in races and also watching the big events. Ive watched it for many years and have been sim racing myself for longer. I tend to stick to iRacing and ACC...
Firstly, this was a really fun experiment which has ended up with a working solution. There is still a lot of work to do on this before it should be considered anywhere near “Production Ready”. Off...
This is a continuation from my previous five posts (Part Zero, Part One, Part Two, Part Three, Part Four ) about the need to have automated way of storing and pull LUKS keys for my servers. In thi...